Data Encryption
What type of encryption does luckycloud use?
At luckycloud, we employ triple encryption to effectively protect your data from hackers, data theft, and data loss:
With server-side TLS and end-to-end encryption, data is encrypted throughout the entire transmission. A cryptographically strong random number is generated and used as a file encryption key. A password further enhances the security of the already complex file key. This is not stored on the luckycloud server. To derive a key/an IV pair from the password, we use the PBKDF2 algorithm. All file data is encrypted with the file key using AES 256/CBC. This results in a so-called encrypted file key. The data is then uploaded and stored. Only you or persons authorized by you can retrieve them with the appropriate file key for decryption. luckycloud has no access to the key and thus no insight into your data. Automatic TLS encryption ensures that no third party intercepts data during transmission.
How do I encrypt my data?
All your data is automatically encrypted with TLS. This prevents third parties from spying on your data. You can apply encryption in the web interface or in the luckycloud client when creating a directory.
Encryption in the Web Interface
- Depending on which luckycloud service you are using, log in to one of the following options:
a. One/Teams: sync.luckycloud.de or directly via our website
b. Business: https://storage.luckycloud
c. Enterprise (Plus): your created cloud domain - Go to "New Directory" (green "+" symbol, top left) and activate "Encrypt."
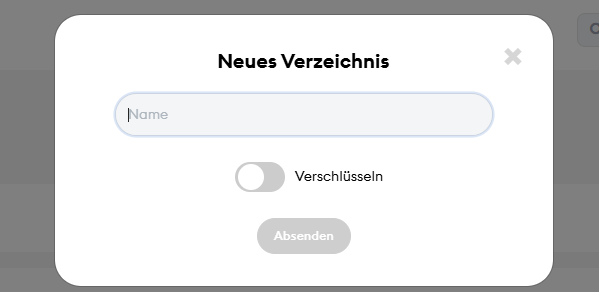
- Now choose a password for your directory and enter it in the appropriate field.
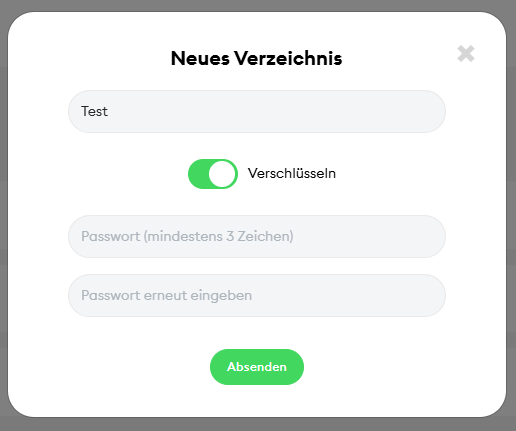
- Complete the process with "Submit."
Only persons who have the associated key can access the directory. If you want to share the directory with other users, you must inform them of the key.
Note: Files and subfolders cannot be encrypted individually. They are automatically encrypted when placed in an encrypted directory. Subsequent encryption and decryption of directories is not possible. The encryption of a directory is like a fingerprint and thus irreversible.
Encryption with the Sync Client
- Open the Sync Client.
- Take the folder you want to upload and drop it into the lower field of the Sync Client.
- A dialog window will appear. Check "Encrypt" and enter a password for the directory. You will need this password to decrypt the directory.
- Complete the process with "OK."
This way, directories are end-to-end encrypted. Only persons who have the associated key can access the directory.
Note: To give you full control over your keys, the keys or directory passwords are not stored on our servers. Password recovery is therefore not possible if you lose the key.
How do I recognize true end-to-end encryption?
You can recognize true end-to-end encryption by the fact that you can choose the key yourself and your key is not stored on the servers (only the corresponding key pair). Thus, the directory password cannot be recovered. Only in this way do you retain control over your data keys!
When is it sensible to encrypt data?
Unlike other cloud providers, luckycloud is a zero-knowledge cloud from Germany. The control over the keys lies with the users. No one can spy on, analyze, or share files. Data monetization is excluded at luckycloud. In case of inquiries and problems, we have only limited access to customer data to provide quick assistance.
If you are unsure which data you should encrypt or if you need help with folder structure, our support team will be happy to assist you.
Note: For encrypted directories, it is not possible to create external sharing links, as a luckycloud user account is required to decrypt the directory. It is also not possible to share individual files or subfolders of an encrypted directory with users, as the entire directory is decrypted during decryption. Therefore, it is all the more important to consider a sensible folder structure beforehand.